WannaCry Ransomware Attack
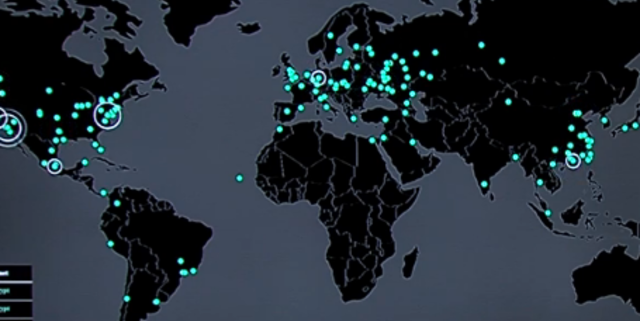
The Wannacry ransomware attack started sweeping through Europe and parts so Asia last Friday. Attacks have also hit here in the US but in far fewer numbers compared to overseas. WannaCry’s hackers that are behind this ransomware are using an exploit in Windows called EtenalBlue that was leaked from the National Security Agency (NSA). Microsoft has known about the vulnerability for about a month. However, not enough people downloaded the patch making thousands of machines vulnerable to this attack. So far, the WannaCry attack has affected 150 countries and thousands of PCs. Once infected the computer displays a lock screen demanding a $300 BitCoin payment in exchange for decrypting the PC’s information. Officials are urging those affected to not pay the ransom demands.
Malware Tech has a real time map of the areas hit by this ransomware. Marcus Hutchins of Malware Tech was able to briefly slow the spread of the attack by identifying a kill switch in the code. His details on his experience can be found on his blog. Now it’s only a matter of time until the coders behind WannaCry remove the kill switches in the code completely rendering newer versions even harder to stop. Cyber security analysts are calling WannaCry a “WMD” of ransomware. It brings to light how dangerous it can be when the NSA’s information is leaked and made public. The dangers of the malware went from data security to possibly effect actual lives when the ransomware locked down systems in hospitals located in the UK. This forced hospital staff to administer care without access to radiology and blood test results. It also required them to cancel critical MRI and CT scans for patients. The ransomware also impacted utilities and government agencies. It’s the worst case of ransomware we have seen to date and brings to light the dangers of leaked classified information and how it can be used maliciously. The dangers and implications of cyber security threats like these spread as quickly as a real life pandemic virus and we should all be made aware of our own cyber security.
WannaCry is also being called WannaCrypt, Wana Decryptor or WCry. The unfortunate success of this ransomware attack is already inspiring copycats. WannaCry makes it easy for these copycats by having a generator that allows you to customize the appearance and script of the lock screen that displays the ransom. So far the known copycats are DarkoderCrypt0r, Aran wanaCrypt0r 2.0 Generator v1.0, WannaCrypt 4.0 and Wana Decrypt0r 2.0.
Home users should ensure their antivirus and Windows OS are up to date in addition to regular backups and adhering to safe internet browsing practices. If you suspect your device has been infected disconnect from your WiFi immediately to prevent the spread to other connected home devices. There is currently no fix available for WannaCry. Antivirus and cyber security companies are hard at work seeking ways to decrypt the files of those infected, but there are no verified working third party decryptions available now.
If you have any concerns about WannaCry’s impact on your business network, please reach out to us to discuss it in further detail. We can assure that Midwest MSP is up to date on all the latest security patches and values your network’s privacy and security.